When you picture a computer hack, you probably think of a guy in a balaclava hunched over a computer screen displaying the code from the movie The Matrix. Or at least you do if you’re a stock photographer.
In truth, most hacks rely on an amount of social engineering, or tricking people in some way to hand over their security details and/or money. Others can rely on malware – software that allows a hacker to access or control your device – and, just occasionally, a whistle obtained from a Cap’n Crunch cereal box.
Back before the era of mobile phones and Voice Over Internet Protocol, making long-distance telephone calls was expensive, involving extra charges on top of the usual rates. It wasn’t a cost that everybody was willing to pay, and a community of “phreakers” sprung up who would attempt to make long-distance phone calls for free by manipulating phone company systems.
Old telephone systems were actually surprisingly easy to mess around with. When an operator (and later, individuals) pushed numbers, they would emit two tones corresponding to the position of the number on the dial pad. Anyone of about 30 and older will be very familiar with the tones these combined frequencies made.
“Now, a lot of people thought and still think that those buttons on the phone actually directly control the phone system. But they don’t. They literally just make sounds,” video game developer and YouTube tech communicator David Murray explained in a talk posted to his channel The 8-Bit Guy.
“The tones is all the phone company cares about and you can actually generate these tones externally.”
It is possible to just record the tones you need onto a cassette tape (if you’re young, picture a Spotify track you had to wind up with a pen) and then play that tape down the phone line the next time you needed to use them.
“The phone company doesn’t care where the tones come from as long as it hears tones that it recognizes.”
Rather than just tape the tones, it was possible to replicate them with instruments. If you knew which tones to play, that meant unlimited free calls to any long-distance number you felt like. Enter Cap’n Crunch.
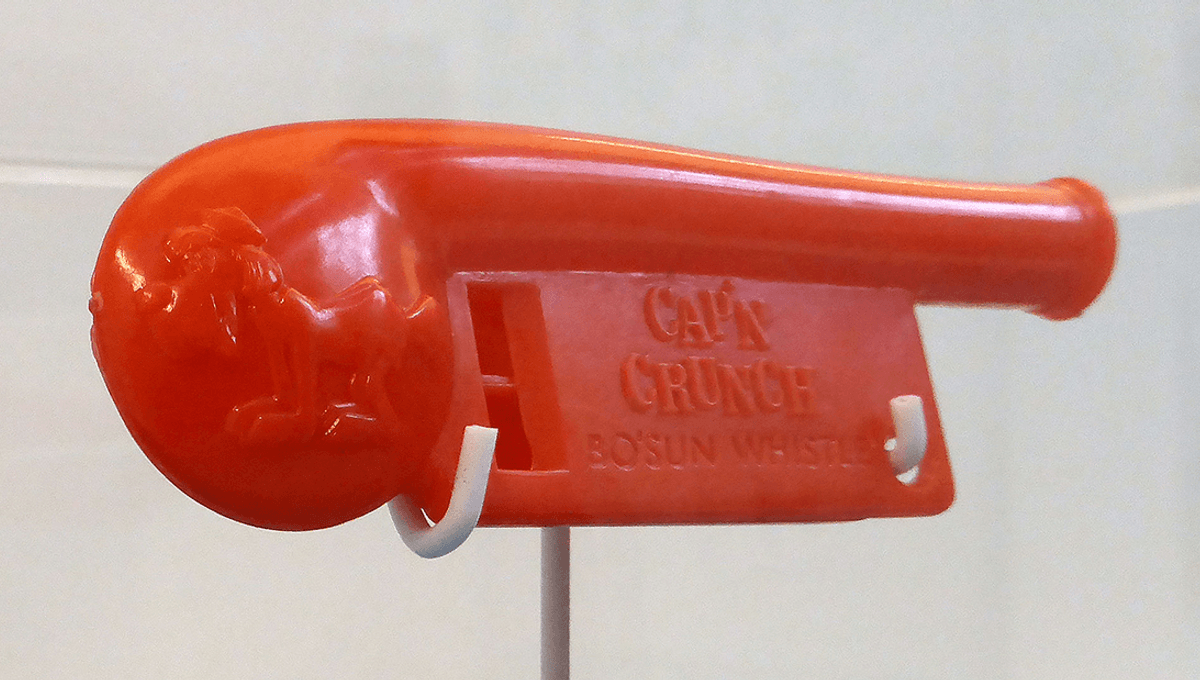
John Draper, a former US Air Force electronics technician and future computer programmer and hacker, noticed that the whistle toys inside Cap’n Crunch cereal packets played perfectly at around the 2,600 hertz needed to hack the phone lines. He used the tones created to make free phone calls over AT&T, and the whistles became iconic in the phreaking community.
While cute, stock photo photographers shouldn’t adjust their catalogs to hackers blowing on slide whistles. It didn’t take long for hackers to come up with an automated system to replace having to manually whistle out a tune every time you wanted to make a phone call, like an elf in a long-distance relationship. Draper created a “blue box” device which could replicate phone company tones.
These boxes caught the attention of Apple founders Steve Jobs and Steve Wozniak in their college days. They went on to build their own versions, selling them around UC Berkeley.
“We built the best one in the world, it was the first digital blue box in the world,” Jobs said in a 1994 interview. “It was the magic of the fact that two teenagers could build this box for $100 worth of parts and control hundreds of billions of dollars of infrastructure in the entire telephone network in the whole world from Los Altos and Cupertino, California. If we hadn’t made those blue boxes, there would be no Apple.”
But it took the beauty out of phone hacking using a cereal toy to make phone calls.
Source Link: One Of The Earliest Hacks Was Performed Using A Cap'n Crunch Whistle Toy